After finding a small typo in the W3C crypto API, and making some contributions to advanced features of Ian Coleman’s BIP39 utility on Github, I was going deep down the crypto rabbit hole of mnemonic recovery phrases for cryptocurrency.
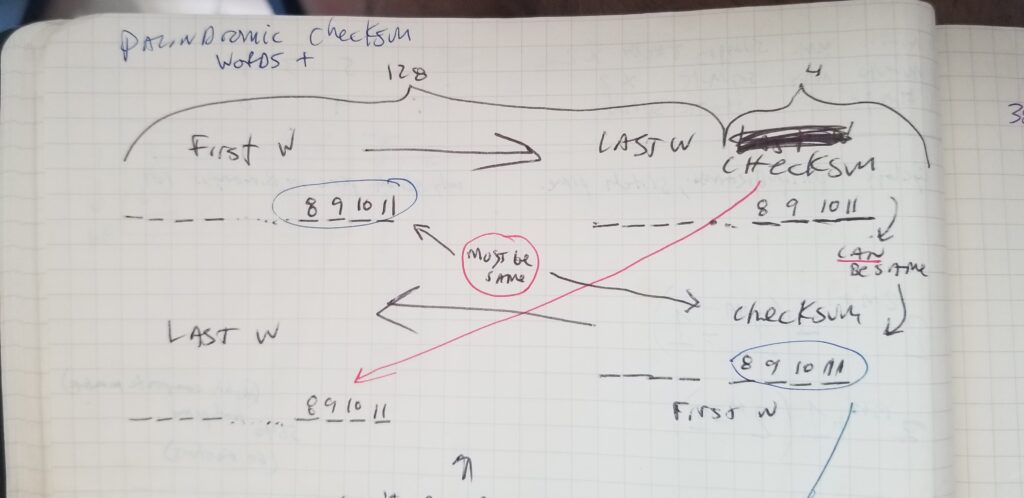
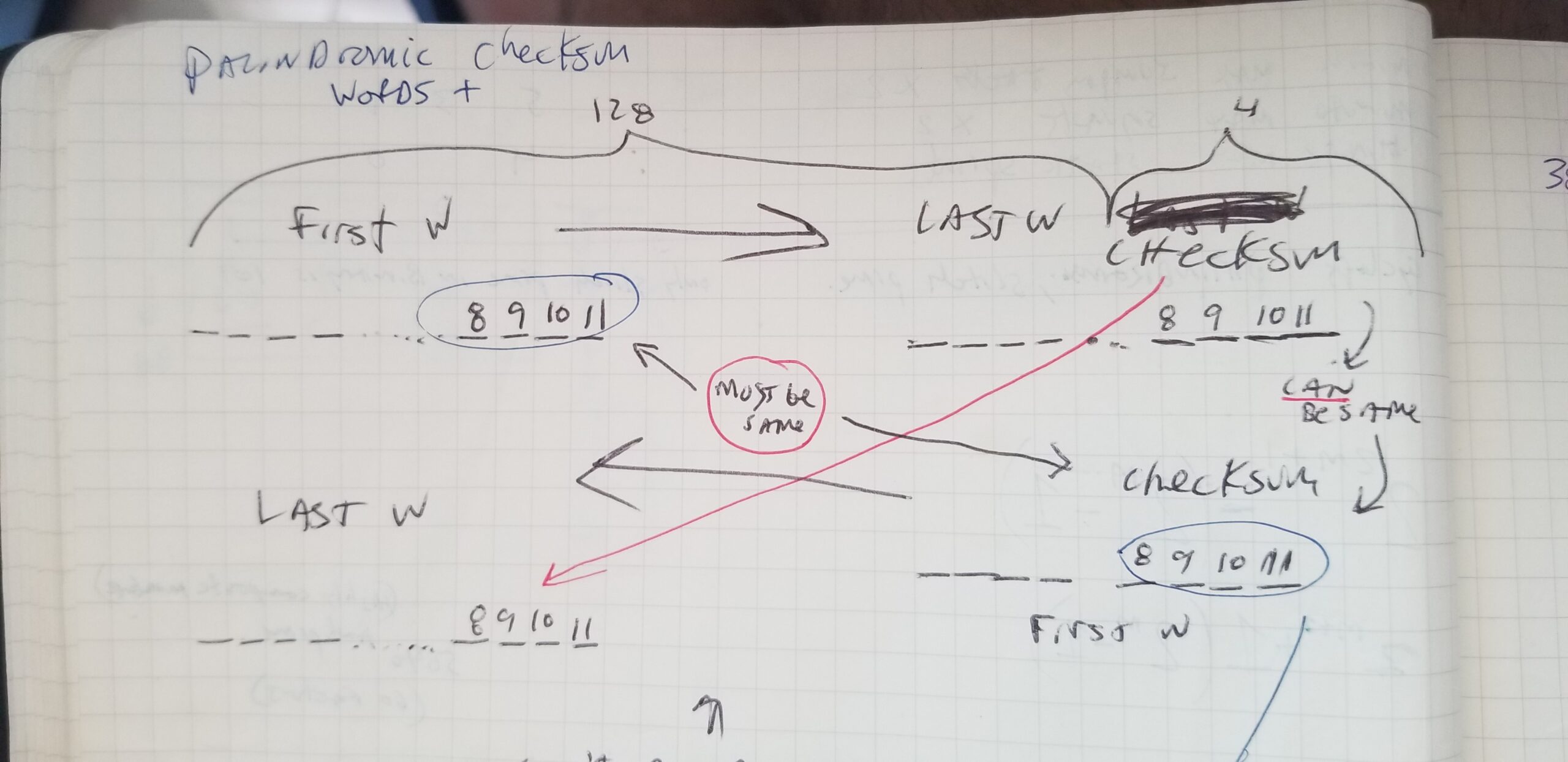
I was thinking long and hard about these structures, binary, hex, bytes, and cryptographic security, and started engineering bits positions on paper while designing what I coined “palindromic mnemonics” aka “reversible recovery phrases.”
The Reversible Mnemonic utility is available here: https://www.stevenhatzakis.com/reversible-bip39-palindromic-mnemonic-recovery-phrase.html
Background: I first shared my design publicly on Gitcoin’s Ambassador repo on Github on November 28th, 2018, and shortly thereafter I had some Python code and pseudo-code that needs a more skilled developer than I to fix, so I posted a bounty on Gitcoin and paid a developer to edit the file I had started. I also shared the idea shortly thereafter with the Bitcoin developer community on the official Linux Foundation Bitcoin dev newsletter.
Adoption of reversible mnemonics
While the Palindromic Mnemonic concept has not become popular or gained adoption, it works and can be used to check existing mnemonics or brute force to find new ones.
Such private key generation tools should always be used offline as a standalone app, to reduce the risk of eavesdroppers or key information leaking, just like when creating a regular mnemonic.
Hatnotation
In terms of backing up entropy or the binary bits that make up a BIP39 mnemonic, I developed a notation scheme called Hatnotation hosted on Github, which allows the user to encode their 132 binary bits into 22 characters, or 264 bits into 44 characters. The idea with this experiment is that Hatnotation creates fewer characters than encoding in Hexidecimal format, for example. Remember, adding complexity to your cryptocurrency backup can lead to lost funds in the event that you forget how to get back to the underlying mnemonic, whether encoded or encrypted with a passphrase or otherwise. For those reasons, the above methods should be considered at best a novelty, such as the emoji mnemonic, or used strictly by advanced users.
About recovery phrases (mnemonics)
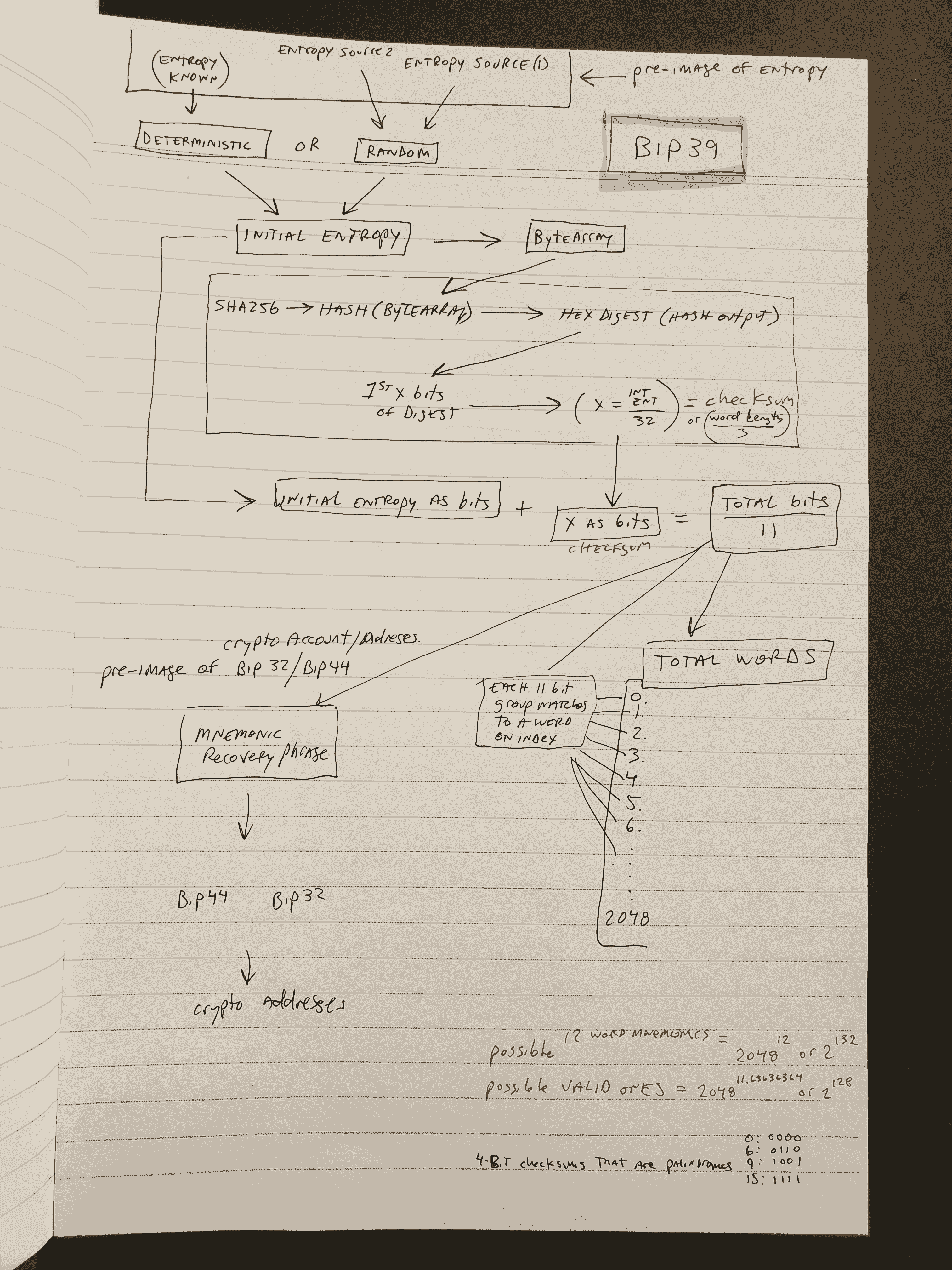
The initial random binary bits “entropy” that are used to create cryptocurrency wallets can be thought of as a pre-image of a SHA256 hash, which is a pre-image of the checksum, where the entropy concatenated with the checksum is what is represented by the resulting mnemonic words.
Therefore, knowing just the entropy is sufficient to recreate the mnemonic, as the checksum is computed deterministically from the SHA256 hash which is created from the initial entropy. Below is a diagram I drew to highlight the above and is the standard used by BIP39 for mnemonic: recovery phrases: